Improving Security With SSO and MFA

Company X provides legal services and content to law firms that require high security to keep legal information confidential. Company X sought to gain the trust of its customers by improving the security of its self-service platform, MyPortal. As a part of this initiative, SSO and MFA would be implemented.
Rollout strategy
We explored several rollout strategies for SSO and MFA. The first phase tied enforcement to each law firm's security requirements—if a firm required it, users went through SSO and MFA. This gave us a clear starting point while leaving room to later offer flexibility for users at firms without strict requirements.
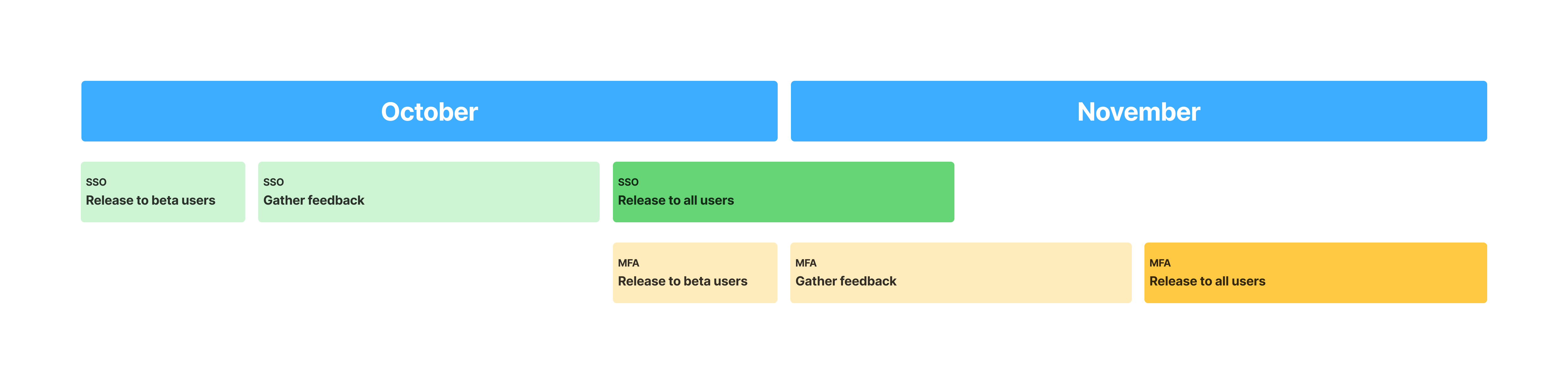
Rollout strategy with phased implementation
Approach
How might we create an SSO and MFA solution that meets enterprise security standards while making the setup and login process intuitive for end users?
Goal 1: Efficient login
Design an efficient login experience with security in mind
Goal 2: Simplified error handling
Provide users with information to understand and resolve errors
Goal 1: Efficient login process
Requirements were still unclear but I created a user flow to align the team. Presenting it to stakeholders and the product manager helped clarify the approach. After refining the flow, we gained buy-in from the technical team to align the approach with the technical implementation.
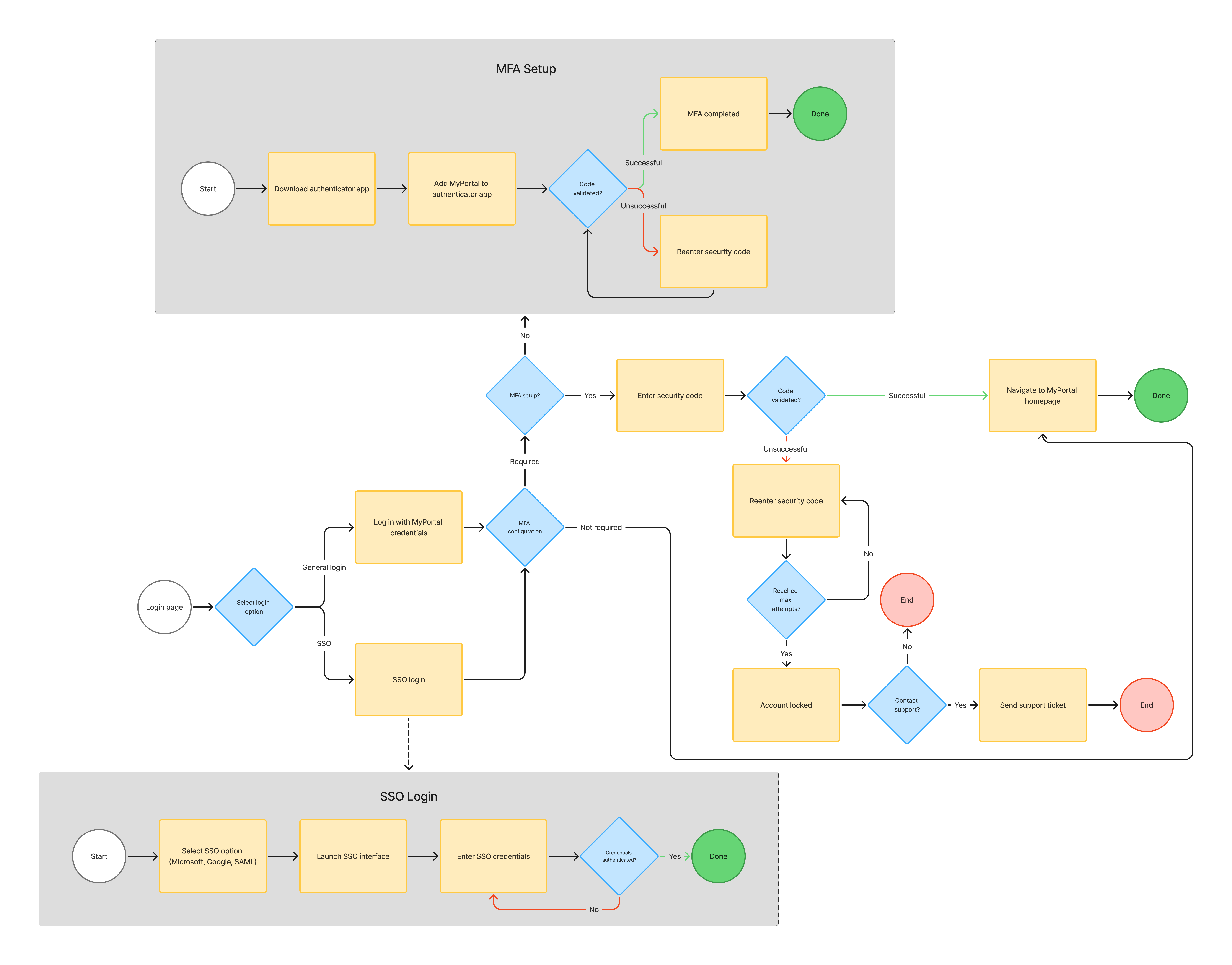
Initial login flow with the addition of SSO and MFA
Goal 2: Simplified error handling
SSO Error 1
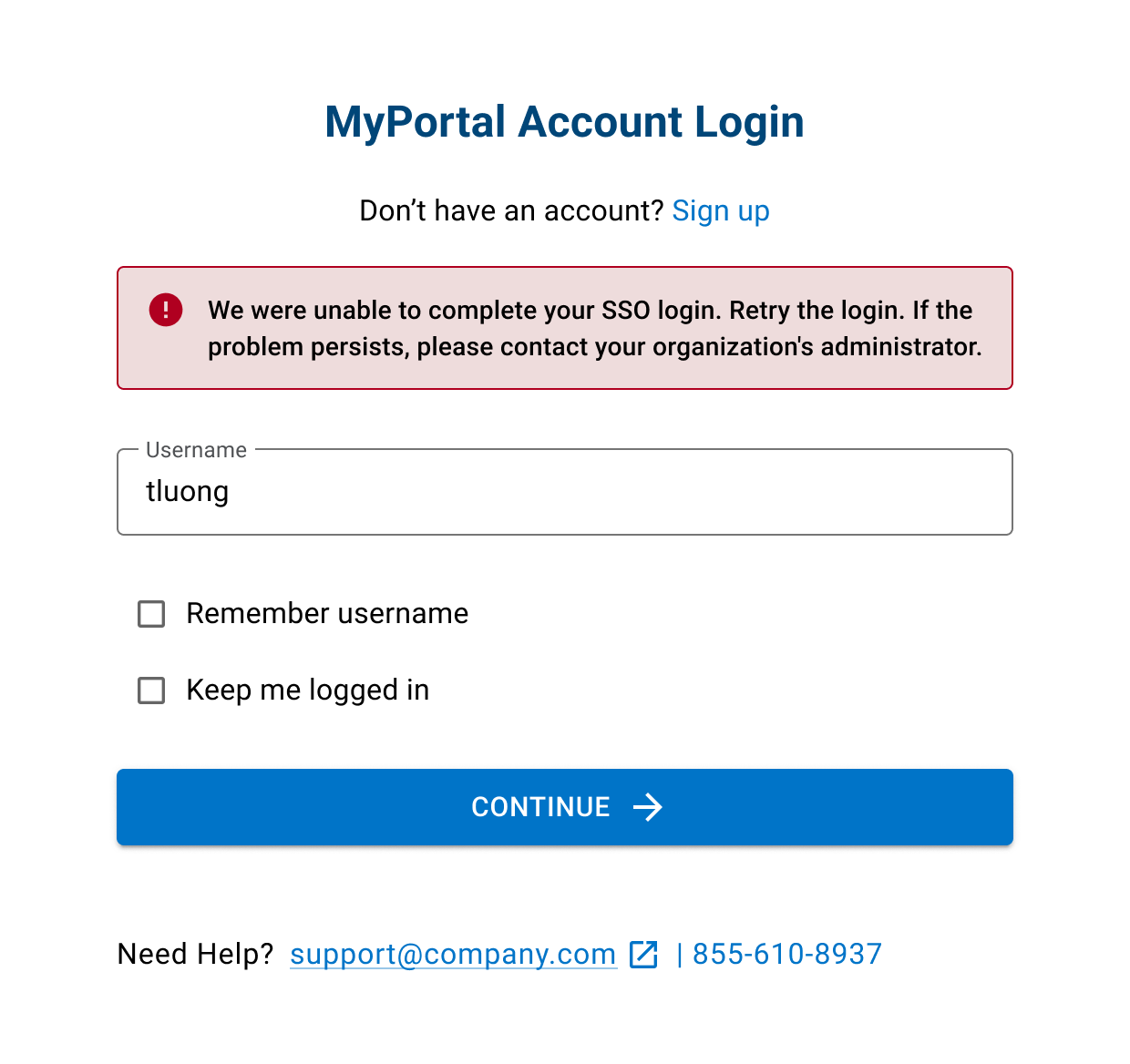
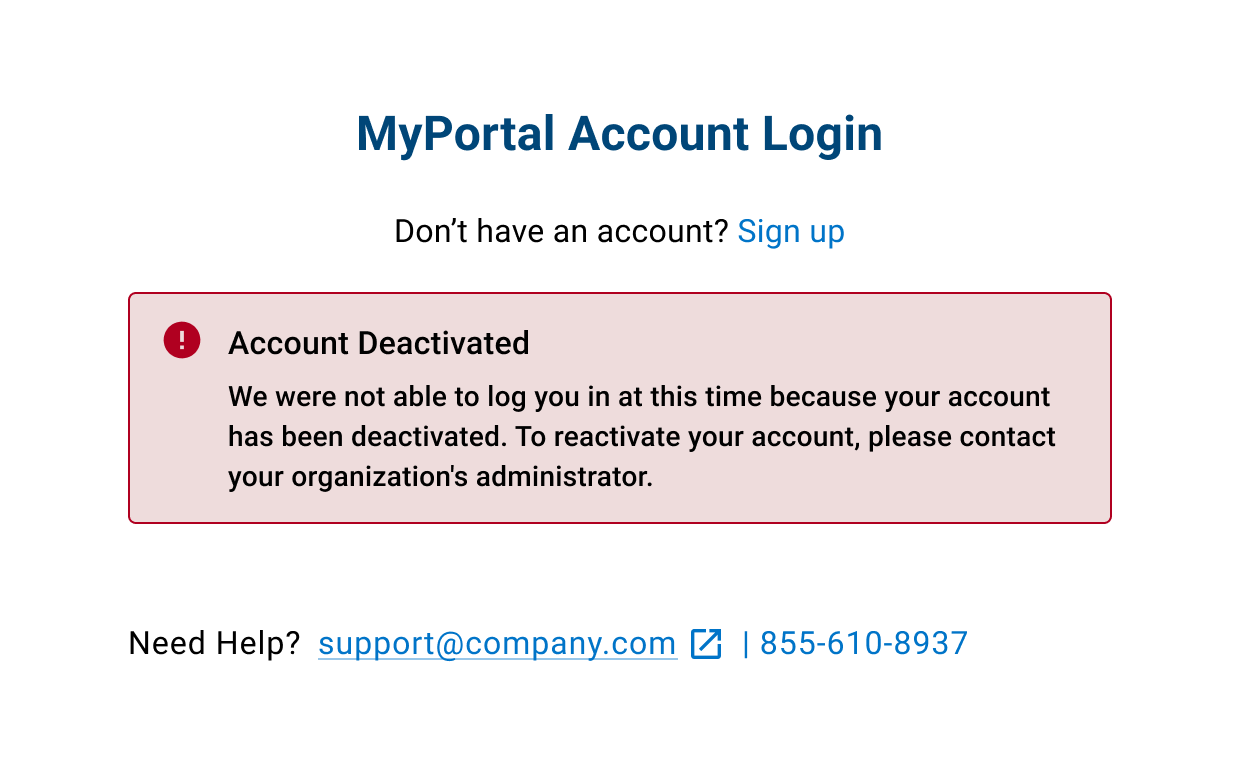
User account is disabled.
SSO Error 2
User account cannot be found.
SSO Error 3
Network or system failure during login.
MFA Error 1
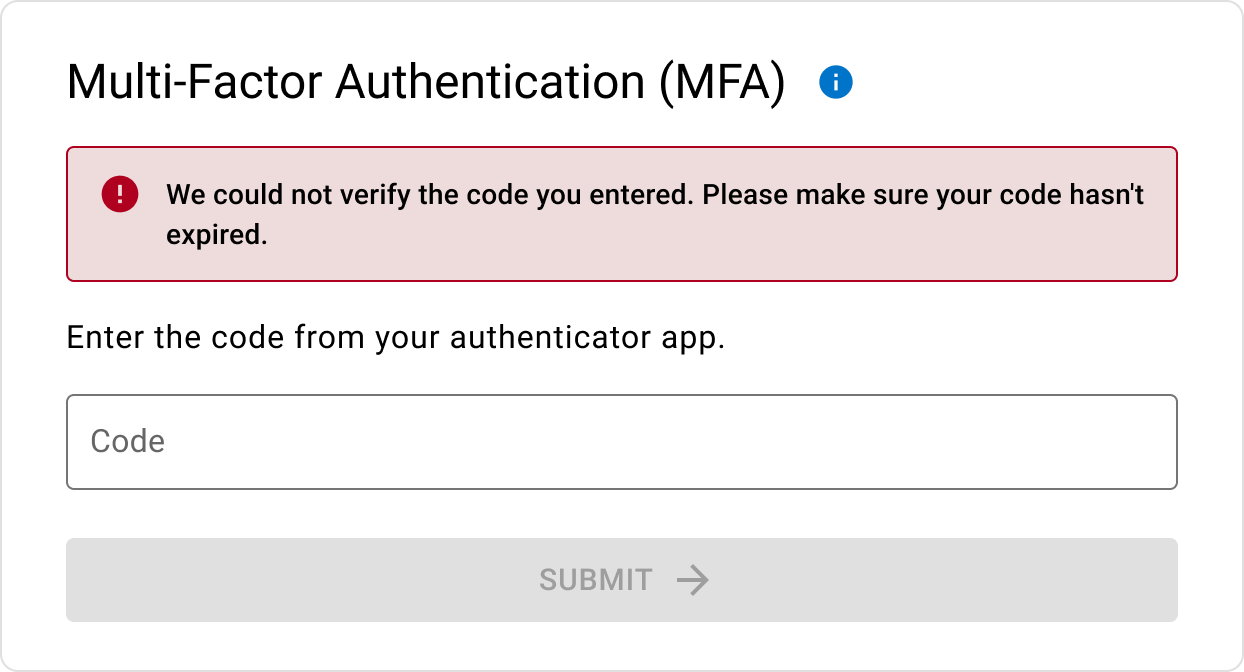
Invalid code entry.
MFA Error 2
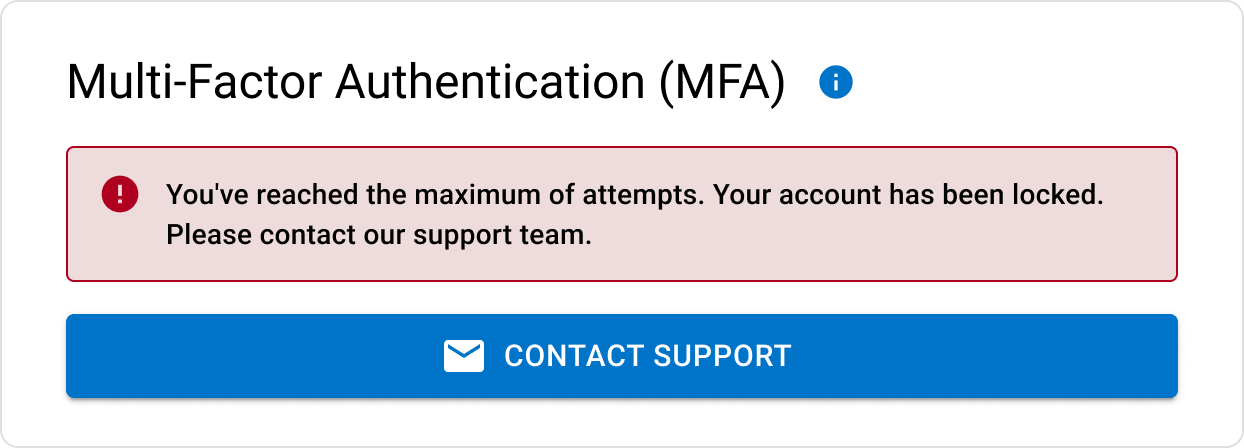
Entered invalid code too many times.
Validating the solution
Mid-fidelity walkthrough
I created mid-fidelity designs to validate the solution. While the user flow validated the approach at a high-level, the design walkthrough helped all team members visualize the solution and understand the end goal.

Wireflow for the login process. Click here to view the FigJam
Validating with the customers
We were unable to perform a usability test with end users. In lieu, we were able to meet with the technical security teams for the law firms interested in this functionality.
The takeaway we got from these meetings were to enforce SSO if the law firm required it. For security reasons, the login options for end users will depend on the law firm’s security requirements.
Pivot! Pivot!! Pivot!!!
Requirements change
Part of the job is to expect the unexpected. Business stakeholders decided to change the requirements by speeding through the roadmap and make MFA optional for all users, rather than based on the law firm’s security requirements. The risks were all on the technical end to quickly fill in the missing pieces.
On the UX front, this was not earth shattering because it’s a common pattern and I was able to make a quick turnaround to adjust the flow. Feedback from the law firms’ technical security teams and the internal business stakeholders converged into a revised user flow.

User flow updates
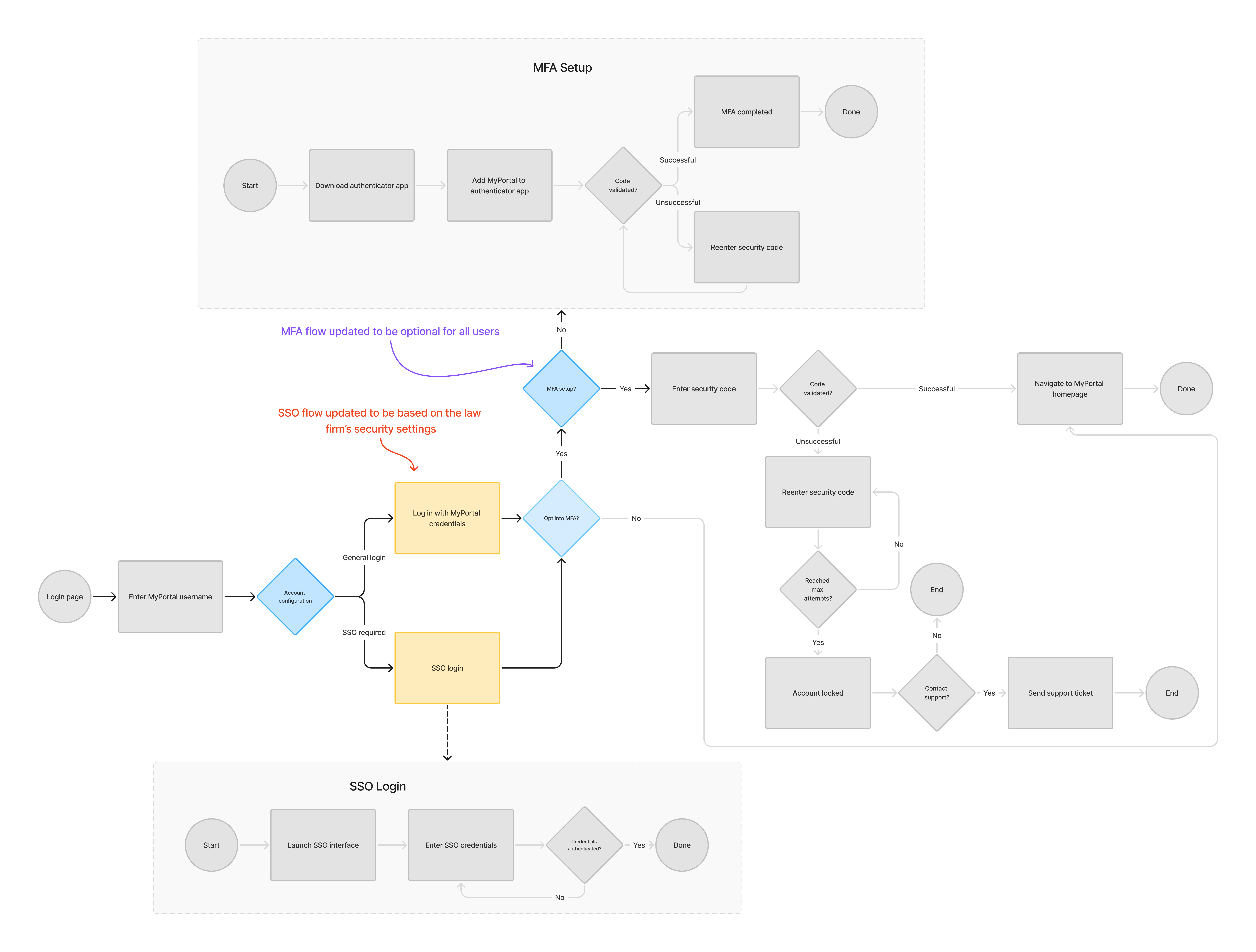
Updated login flow to base SSO on the law firm's security requirements. Click here to view the FigJam
Design updates
Checking username for SSO configuration
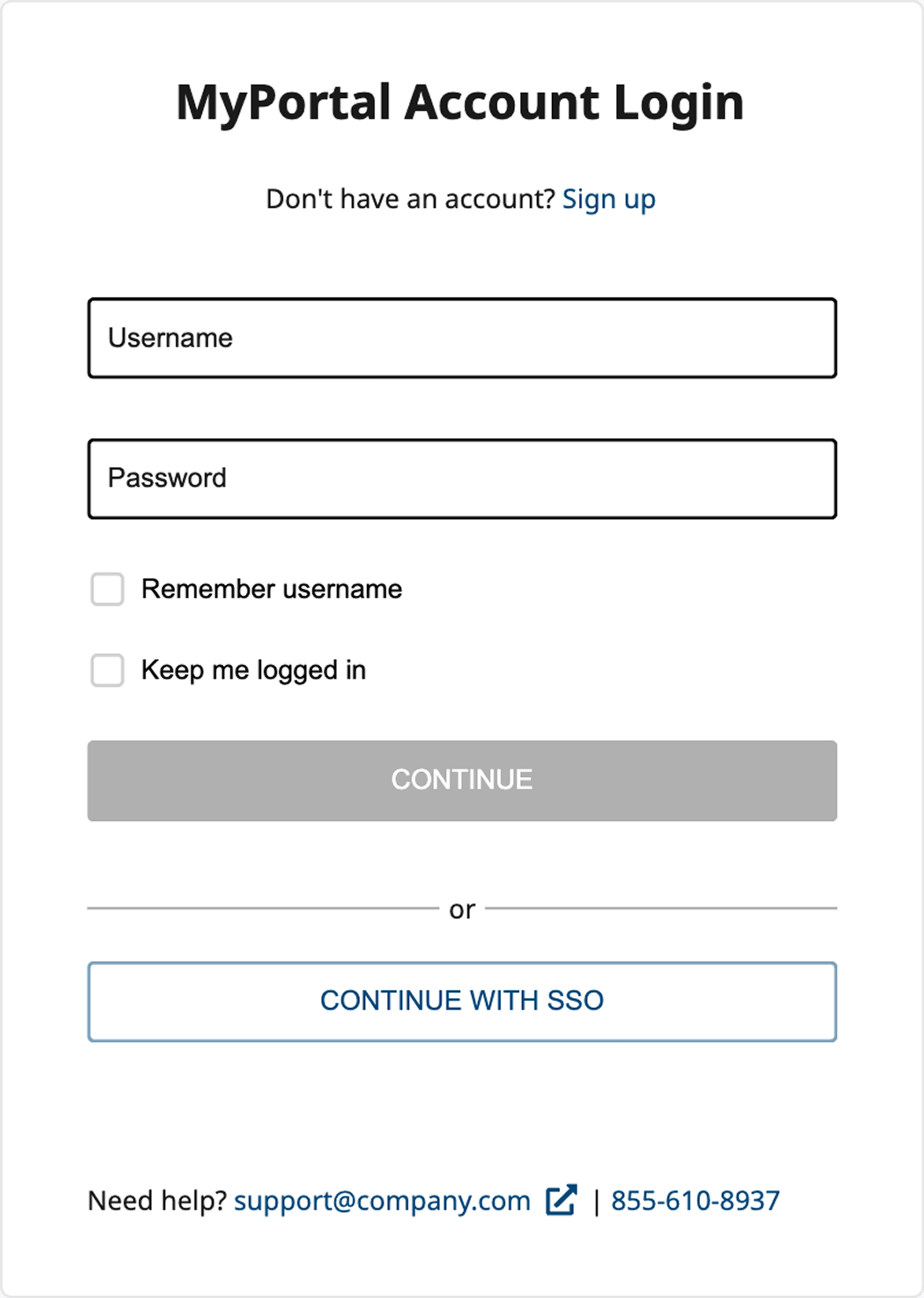
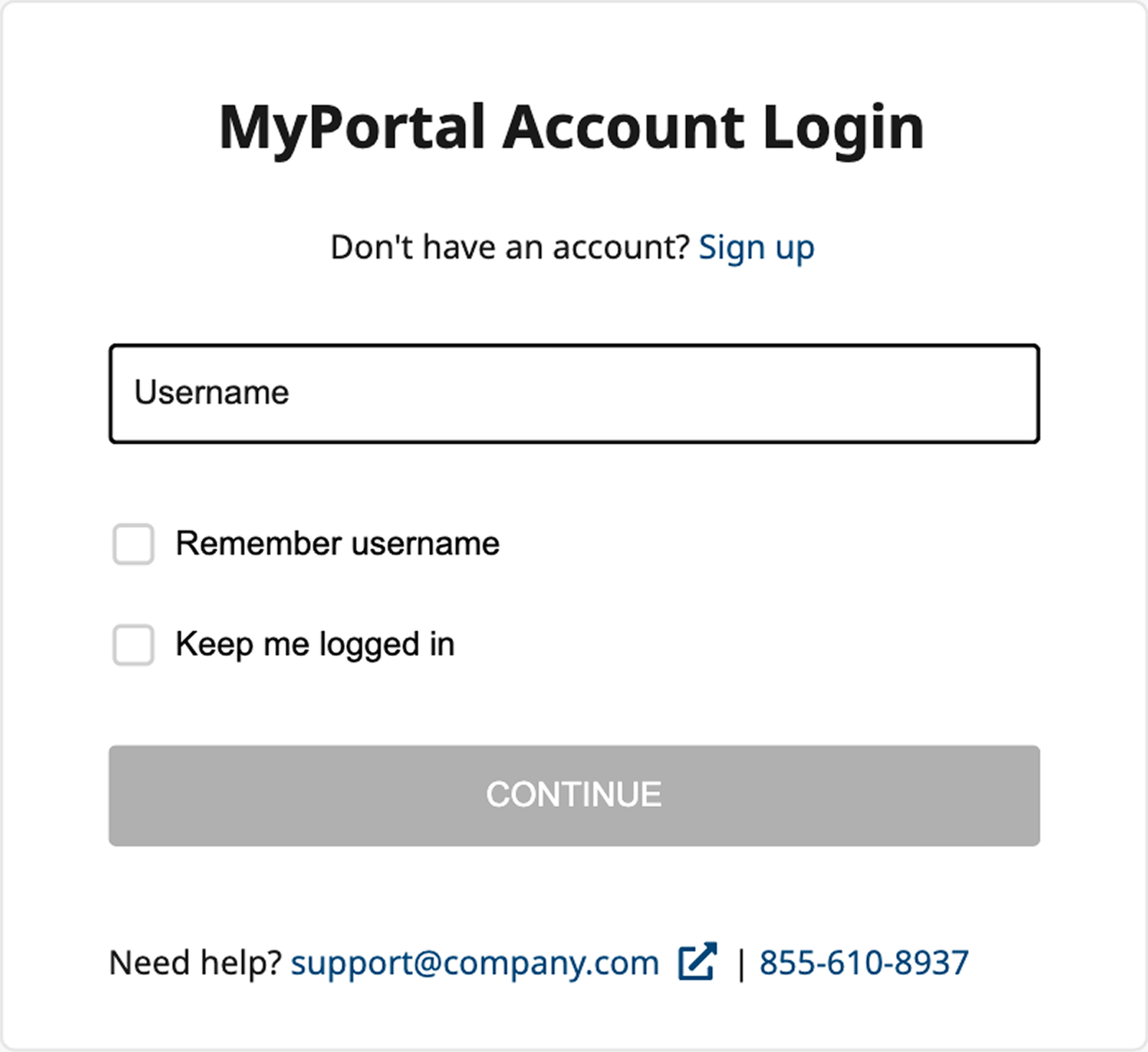
Option to skip MFA setup
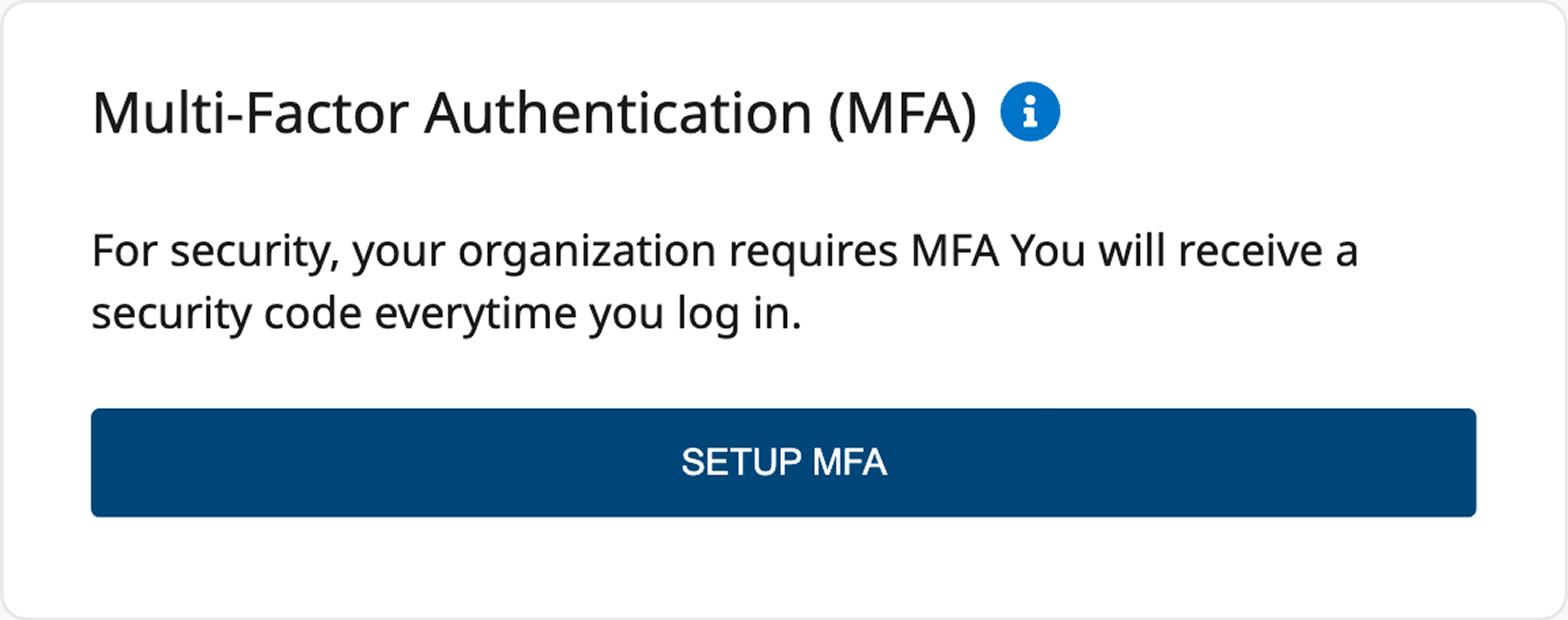
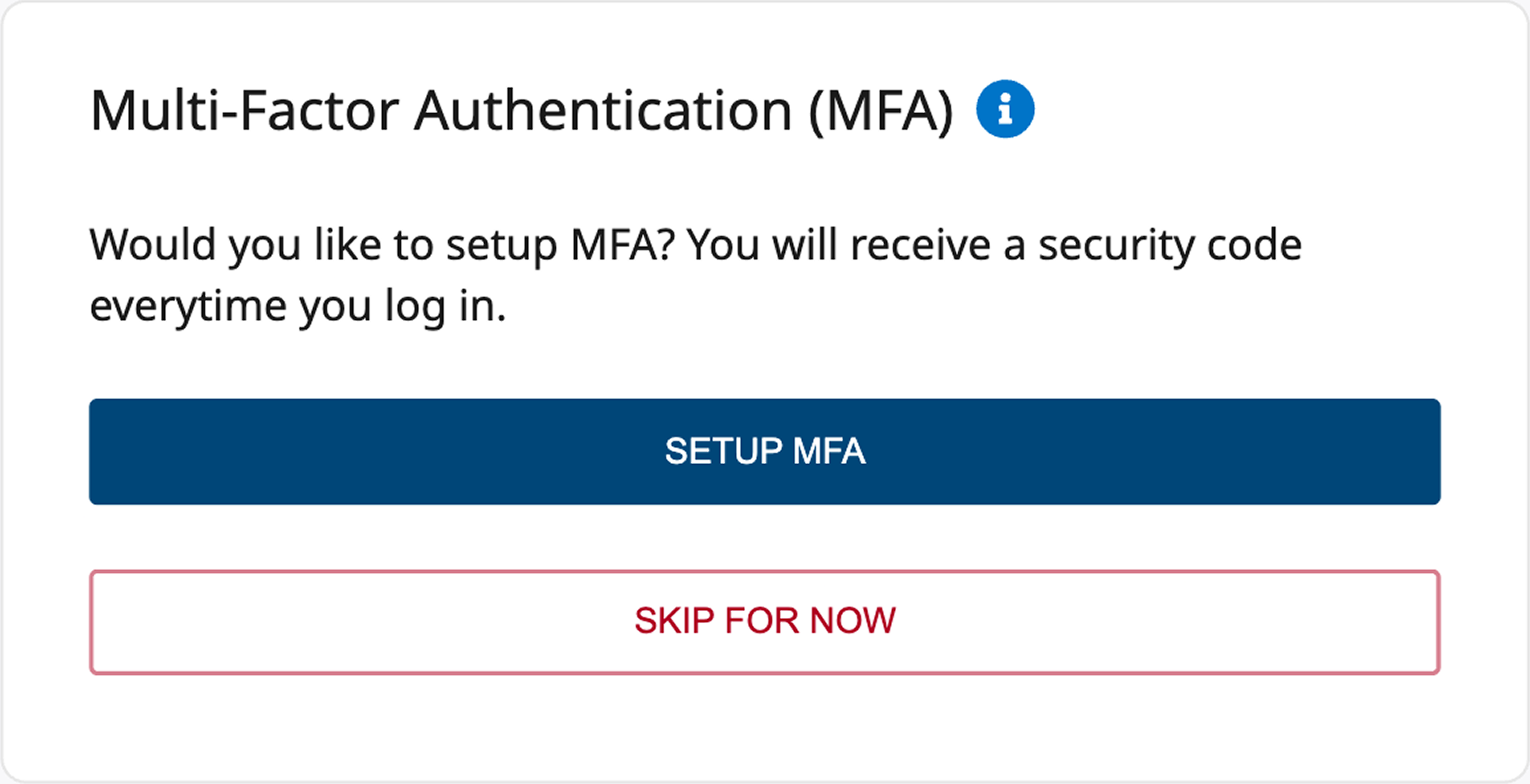
Finalized error messaging
SSO error states
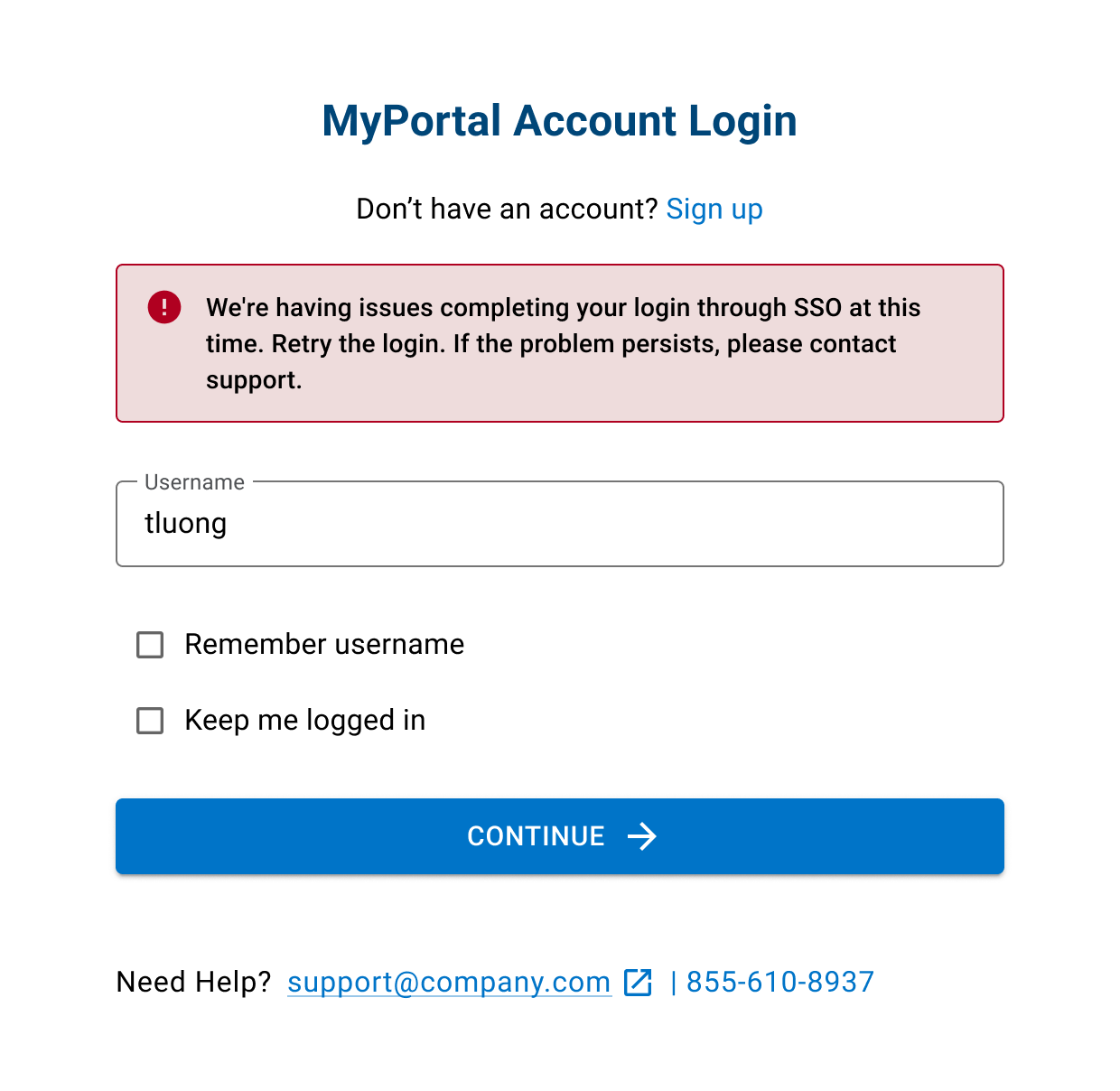
MFA error states
Final walkthrough
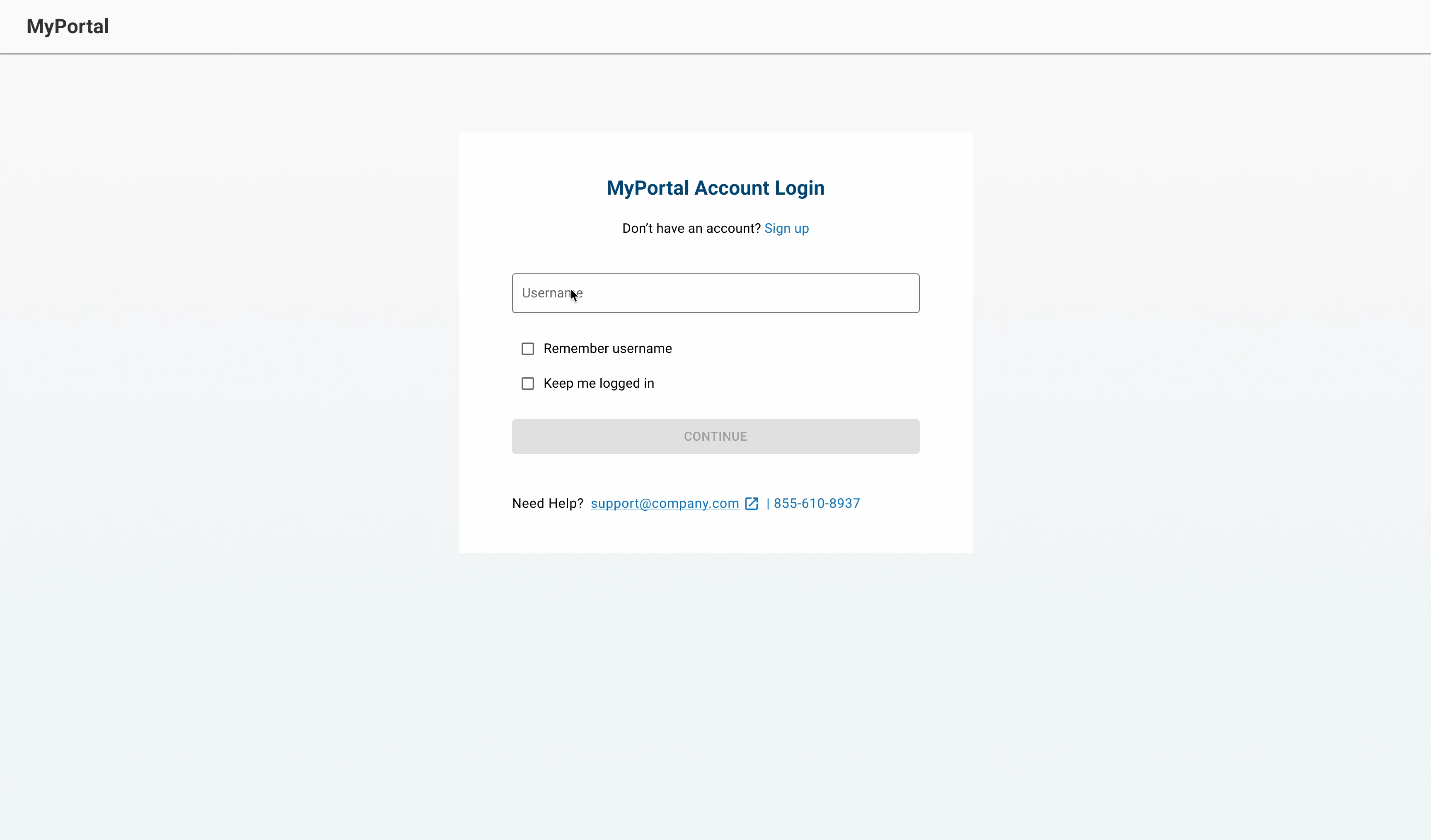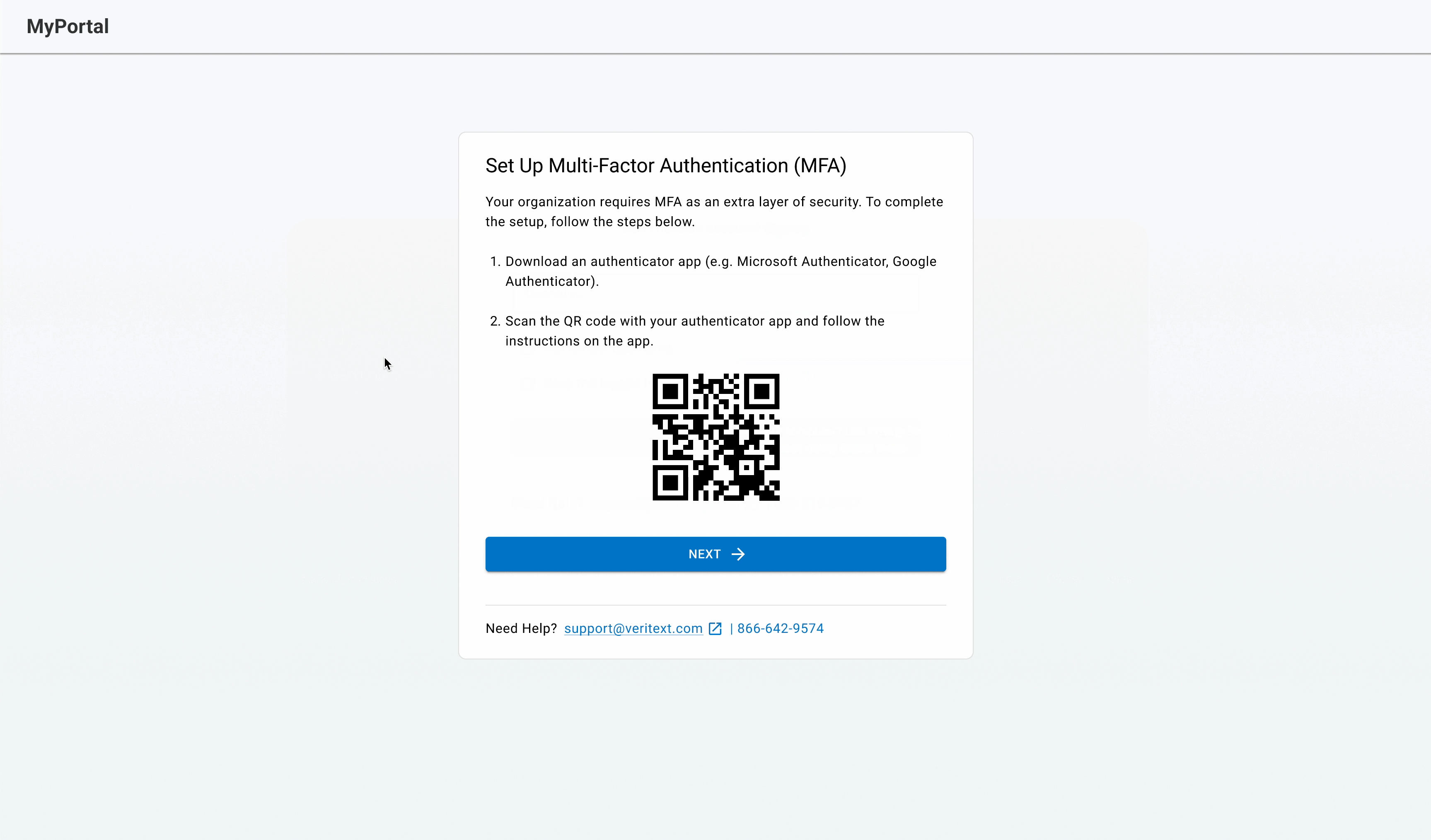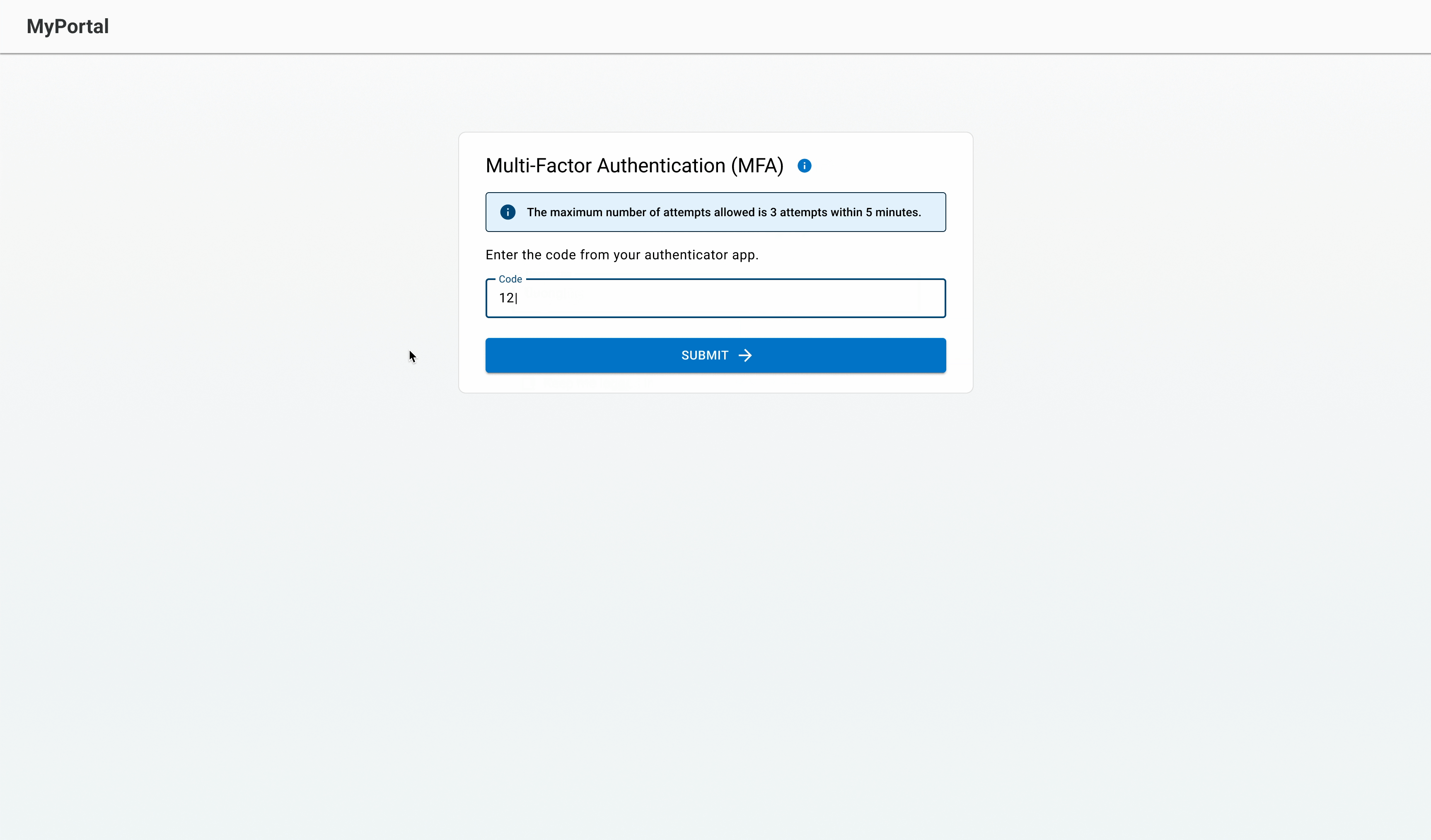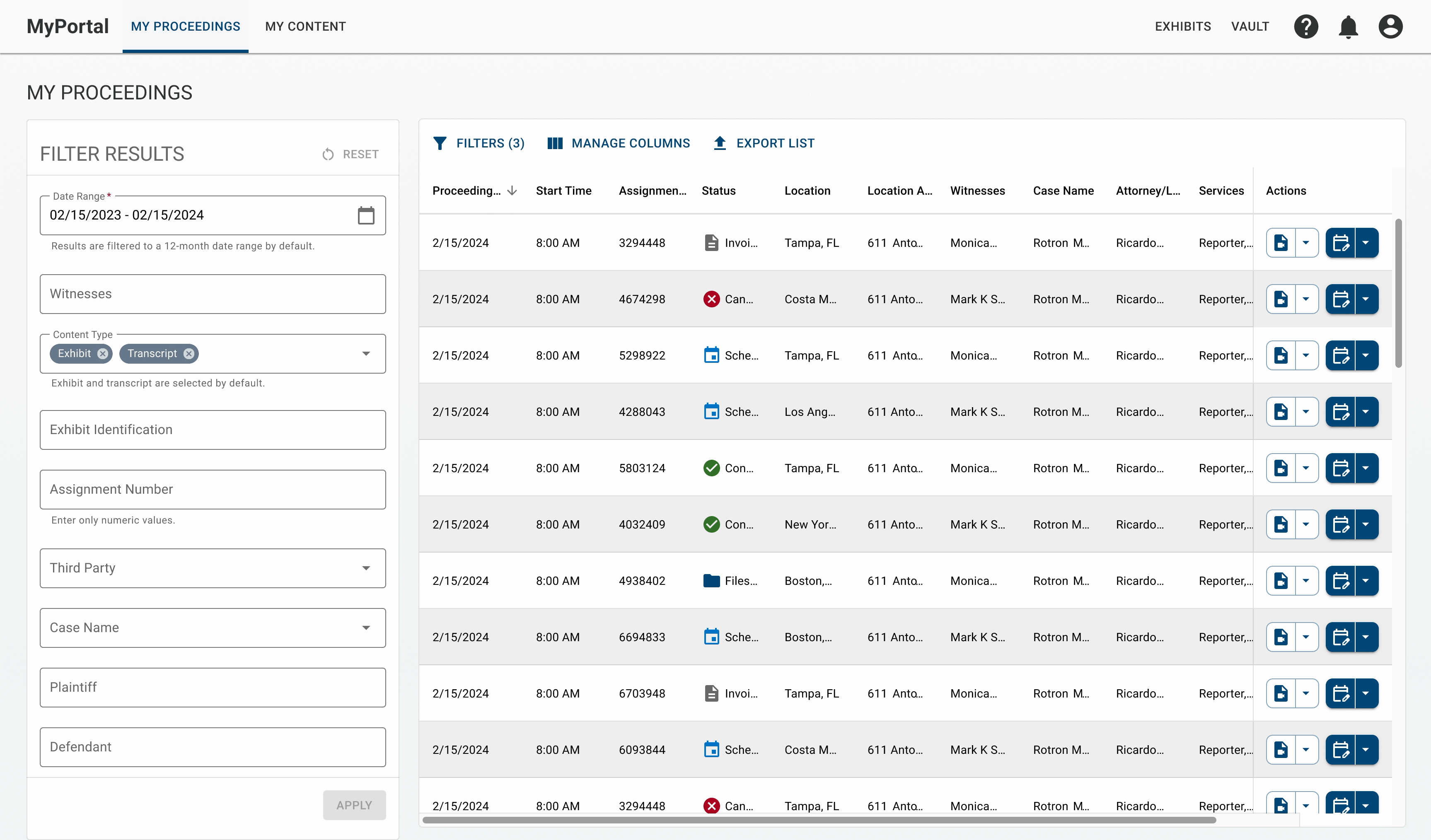
Beta user feedback
At the time of writing this case study, the feature was in the beta rollout phase and the beta users provided positive feedback.
“The login process feels easy, there's no surprises.”
“This is exactly what we needed to improve the security at the firm.”
Next steps
To support SSO management, the team will be working on a feature for NetOps users to manage SSO configurations for all active clients.
Once the feature rolls out to all users, the team will be using Datadog to monitor for performance issues and Jira Service Management to track bugs and usability issues.
Reflection
Overall, this project has been a success so far. I was able to be efficient by leaning into user flows and mid-fidelity methods, to validate requirements. SSO and MFA are seemingly simple, however, the technical implementation needed to be discussed. As evidenced by the frequent requirements change, this was an effective and efficient method to ensure the team was aligned.